Bitcoin: Part 33
Bitcoin Self-Custody: A Deep Dive into Keys, Wallet Types, Securing BTC, Transactions, and UTXOs
If you’ve bought Bitcoin and left it on an exchange, congratulations — you own a Bitcoin IOU. But if you’ve moved your BTC to a wallet, then you truly own sovereign money. This is self-custody. Bitcoin’s promise of financial sovereignty hinges on self-custody — taking full control of your assets without relying on third parties. But with great power comes great responsibility. This post explores the nuts and bolts of Bitcoin self-custody, covering keys, wallet types, securing your BTC, transactions, and UTXOs. Whether you are new to Bitcoin or a seasoned hodler, this guide will help you navigate the complexities of managing your own funds securely.
🔑 Understanding Bitcoin Keys
At the heart of Bitcoin self-custody are cryptographic keys. These keys are what allow you to control and spend your Bitcoin.
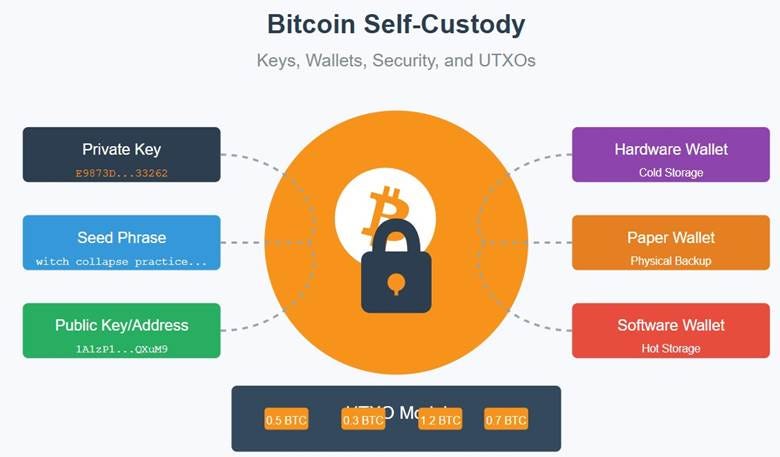
Private Keys: A private key is a randomly generated 256-bit number that grants ownership of a Bitcoin address. Think of it as the ultimate password to your funds. If someone gets your private key, they control your Bitcoin. If you lose it, your funds are gone forever.
Public Keys and Addresses: From your private key, a public key is derived using elliptic curve cryptography (secp256k1). The public key is then hashed to create a Bitcoin address (e.g., starting with "1", "3", or "bc1"). You share the address to receive BTC, but the private key must remain secret.
Seed Phrases: Most wallets generate private keys from a seed phrase (typically 12 or 24 words). This mnemonic, based on the BIP-39 standard, is a human-readable backup of your keys. Write it down, store it securely, and never share it.
Key Takeaway: Your private keys or seed phrase are your Bitcoin. Protect them like your life depends on it.
🧳 Types of Bitcoin Wallets
Bitcoin wallets come in various forms, each balancing convenience, security, and control. A wallet doesn’t store BTC (Bitcoin lives on the blockchain); it manages your keys and helps you interact with the network.
1. Software Wallets
Hot Wallets: Connected to the internet, making them convenient but less secure. Examples include mobile apps (e.g., BlueWallet, Muun, or Phoenix), desktop wallets (e.g., Electrum, Sparrow), and browser extensions like MetaMask (for ETH – not ideal for BTC). Best for small amounts or daily use.
Pros: Easy to use, fast transactions.
Cons: Vulnerable to hacks, malware, phishing, or device compromise.
2. Hardware Wallets
Cold Wallets: Offline devices like Trezor, Ledger, or Coldcard that store keys securely. Transactions are signed offline, reducing exposure to online threats.
Pros: High security, ideal for long-term storage.
Cons: Costly (typically $50-$150) and more complex to use especially for beginners.
3. Paper Wallets
A paper wallet is simply a private key or seed phrase written on paper, stored offline. You can generate one using tools like Bitaddress.org (offline only).
Pros: Extremely secure if generated and stored properly.
Cons: Prone to physical damage, loss, or user error when spending.
4. Multisig Wallets
Multisignature wallets (BIP-48) require multiple private keys to authorize a transaction (e.g., 2-of-3 keys). They’re ideal for advanced users or shared custody.
Pros: Enhanced security, protection against single-point failures.
Cons: Complex setup, slower transactions.
Key Takeaway: Choose a wallet based on your needs. Hardware wallets are the gold standard for most users, while multisig offers advanced security for larger holdings.
🔐 Securing Your Bitcoin
Self-custody means you’re your own bank, so security is paramount. Here are best practices to protect your BTC:
Backup Your Seed Phrase: Write down your 12/24-word seed phrase on paper or metal (e.g., Billfodl or CryptoSteel). Store copies in multiple secure locations (e.g., a safe, a bank vault). Never store it digitally or take photos.
Use Strong Passphrases: Some wallets support BIP-39 passphrases, an optional extra word that adds a layer of security. This creates a “hidden wallet” separate from your main wallet.
Physical Security: Keep your hardware wallet and seed phrase backups in tamper-proof, fire-resistant storage. Avoid obvious hiding spots.
Never share your seed: Not with anyone. Ever.
Avoid Phishing: Only download wallet software from official sources. Verify URLs and use bookmarks to avoid fake websites. Never enter your seed phrase online.
Test Your Setup: Send a small amount of BTC to your wallet, wipe the device, and restore it using your seed phrase to confirm your backup works.
Run Your Own Node: For maximum privacy and verification, run a full Bitcoin node (e.g., Umbrel, Start9, etc.). This lets you validate transactions without trusting third-party servers.
Consider multisig: It protects you from single points of failure.
Key Takeaway: Security is a mindset. Layer multiple protections and always assume you’re a target.
🧱 Transactions and UTXOs Explained
Bitcoin transactions are how you move BTC on the blockchain. Understanding them is crucial for efficient self-custody.
What Are UTXOs?
UTXO stands for Unspent Transaction Output. Think of UTXOs as individual “chunks” of Bitcoin you own, each tied to a specific transaction output.
Example: If you receive 0.5 BTC and later 0.3 BTC, you have two UTXOs (0.5 and 0.3). When you spend, you must use entire UTXOs, and any “change” creates a new UTXO.
Why It Matters: UTXOs affect transaction fees and privacy. Combining many UTXOs increases transaction size, raising fees. Coin control (available in wallets like Sparrow) lets you choose which UTXOs to spend for efficiency.
📤 How Transactions Work
Inputs and Outputs: A transaction spends UTXOs (inputs) and creates new ones (outputs). For example, to send 0.4 BTC, you might use a 0.5 BTC UTXO, sending 0.4 BTC to the recipient and 0.1 BTC back to yourself as change (minus fees).
Fees: You pay miners a fee (in satoshis per byte) to prioritize your transaction. Use wallets with dynamic fee estimation to avoid overpaying or delays.
Signatures: Your wallet signs the transaction with your private key, proving you own the UTXOs. Hardware wallets sign offline for added security.
Broadcasting: The signed transaction is broadcast to the Bitcoin network, where nodes validate it and miners include it in a block.
When you send BTC:
Your wallet signs a transaction with your private key.
It selects one or more UTXOs to spend.
It defines outputs — one to the recipient, one back to you as change.
It broadcasts the transaction to the Bitcoin network.
Miners validate, confirm, and add your transaction to the blockchain.
Fees depend on transaction size (in bytes) and network congestion. Tools like mempool.space can help you estimate the right fee.
🛡️ Privacy Tips
Avoid address reuse: Sending BTC to the same address multiple times links your transactions, reducing privacy.
Use SegWit addresses (starting with “bc1”): They’re cheaper and more efficient.
Label UTXOs: Some wallets let you tag UTXOs to avoid combining unrelated funds, which can leak information.
Key Takeaway: Master UTXOs and coin control to optimize fees and protect your privacy.
₿ Common Pitfalls and How to Avoid Them
Losing Your Seed Phrase: Without it, your BTC is unrecoverable. Always back up and test your recovery process.
Trusting Custodians: Exchanges and custodial wallets can freeze or lose your funds. “Not your keys, not your crypto.”
Ignoring Updates: Keep your wallet software and firmware updated to patch vulnerabilities.
Rushing Transactions: Double-check addresses and fees. Bitcoin transactions are irreversible.
Overcomplicating: Multisig and advanced setups are great but can overwhelm beginners. Start simple and scale up.
🧠 Final Thoughts
Bitcoin self-custody is empowering but demands diligence. By understanding keys, choosing the right wallet, securing your funds, and mastering transactions, you can take full control of your financial future. Start small, test everything, and never stop learning. The Bitcoin rabbit hole is deep, but the rewards of sovereignty are worth it.
Additional Resources
Disclaimer:
This article provides educational information, not financial or security advice. Always conduct your research and consider consulting professionals before implementing cryptocurrency security systems.